Scenario: Unfortunately it doesn’t look like I’m able to go back and grab information once I complete the challenge. Basically, the organization has been informed by their MSP that their host and network based firewalls have incomplete configurations. My task was to go on the available systems and ensure only the ports recommended by the MSP were available and reachable.
Network Map:
Upon reviewing the meeting notes, the following table was made to document the host firewall rules that would need to be added to specific hosts within the network.
| Host | IP | Ports |
| Prod-Joomla | 172.16.10.100 | SSH(22), HTTP(80)*, HTTPS (443)*, RELATED,ESTABLISHED |
| Workstation | 172.16.20.60 | NETBIOS(137), SMB(445), 5985 |
| AD-Server | 172.16.30.55 | 88, 135, 389, 445, 636, 3268-3269, 49152-65535, DNS |
| Fileshare | 172.16.30.100 | SSH(22), NETBIOS(137), SMB(445) |
| Database | 172.16.30.88 | RPC(135), NETBIOS(137), SMB(445), MySQL(3306) |
* Port should be reachable by external networks
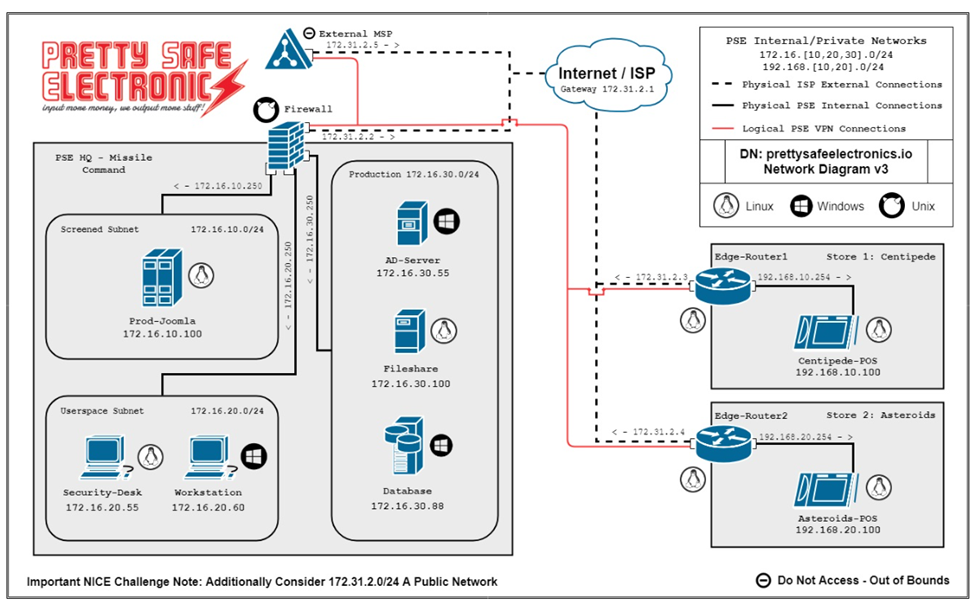
Starting on Prod-Joomla, I observed the tool IPTABLES was present on the system. There were no rules established at the time of configuration. IPTABLES rules were added as shown here:
- ALLOW any RELATED or ESTABLISHED connections.
- ALLOW any HTTP connections.
- ALLOW any HTTPS connections.
- ALLOW SSH connections only from the USERSPACE subnet.
- ALLOW any connections from the MSP IP address.
- LOG any additional connections not otherwise allowed.
- DROP any additional connections not otherwise allowed.
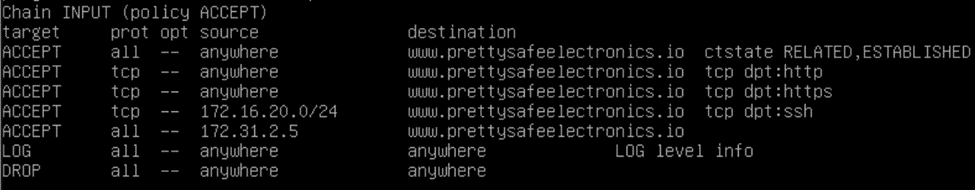
I next moved on to Fileserver. I observed the tool IPTABLES was present on the system. There were no rules established at the time of configuration. IPTABLES rules were added as shown here:
- ALLOW any RELATED or ESTABLISHED connections.
- ALLOW SSH connections only from the USERSPACE subnet.
- ALLOW any NETBIOS connections.
- ALLOW any SMB connections.
- ALLOW any connections from the MSP IP address.
- LOG any additional connections not otherwise allowed.
- DROP any additional connections not otherwise allowed.
For the Workstation, the Windows Defender Firewall was used to add rules. A Single rule was added that contained all the ports specified as per the MSP. Additionally, each profile had logging enabled for dropped packets.
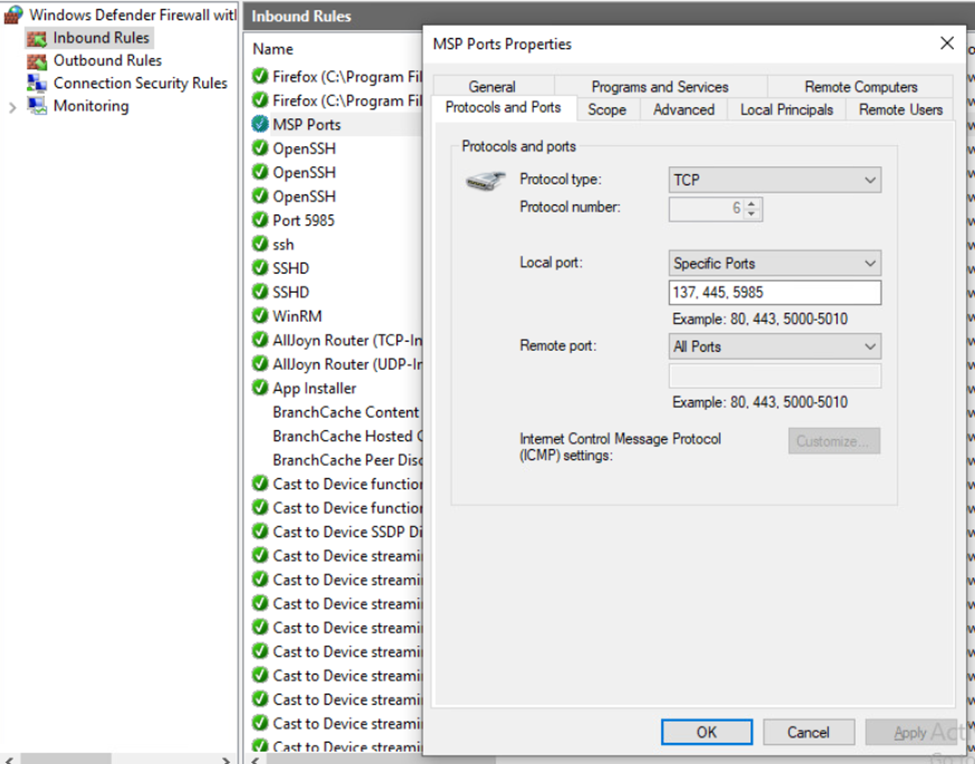
For the Database, the Windows Defender Firewall was used to add rules. A Single rule was added that contained all the ports specified as per the MSP. Additionally, each profile had logging enabled for dropped packets.
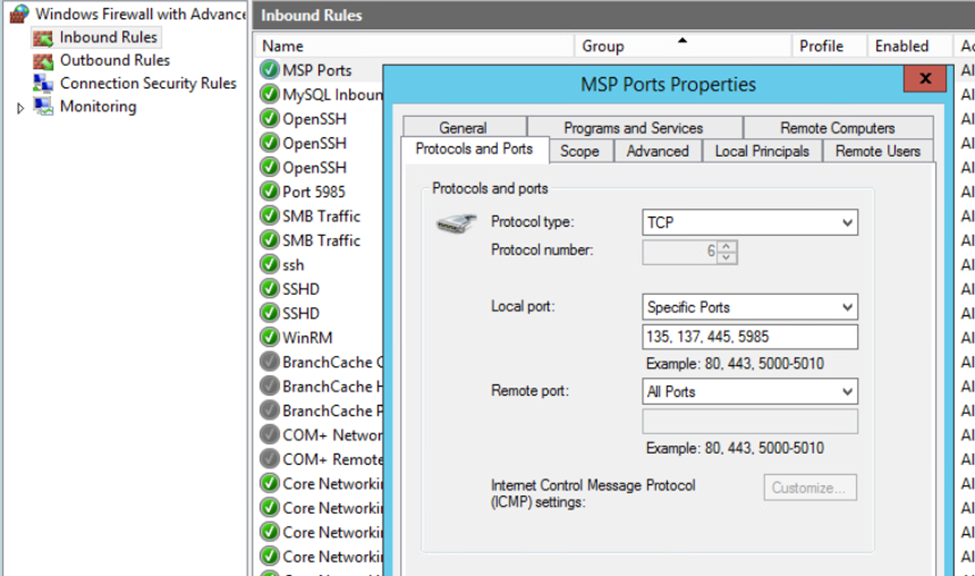
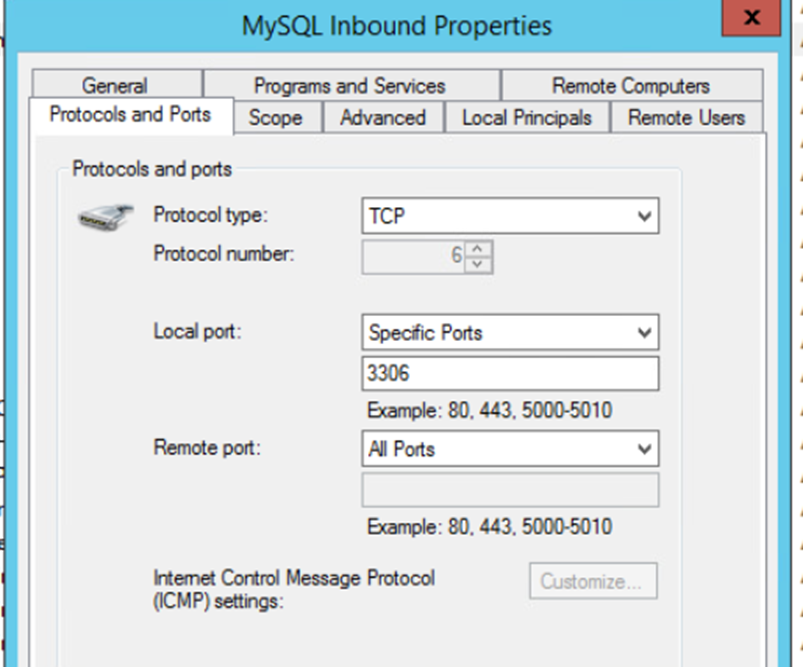
A rule for MySQL rules was already present.
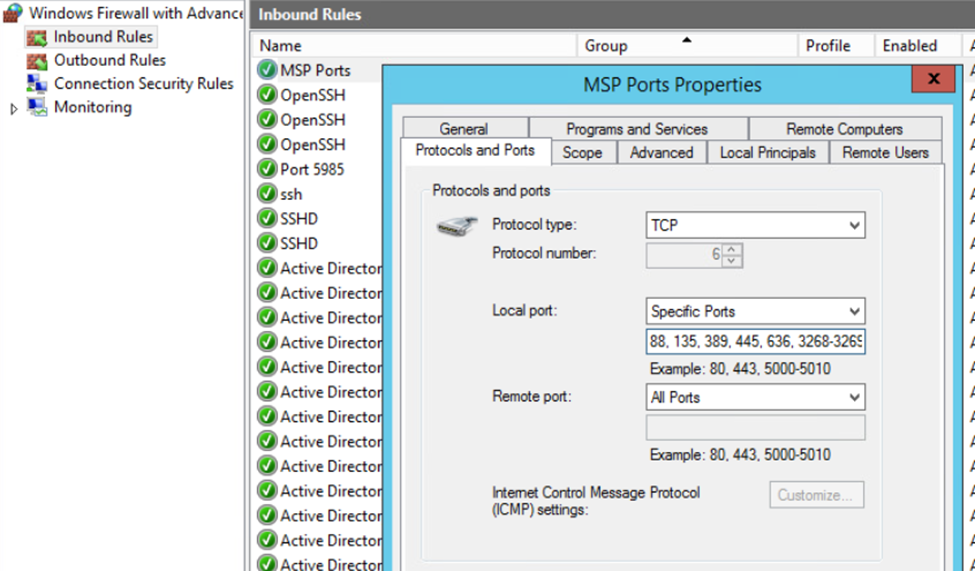
For the AD-Server, the Windows Defender Firewall was used to add rules. A Single rule was added that contained all the ports specified as per the MSP. Additionally, each profile had logging enabled for dropped packets.
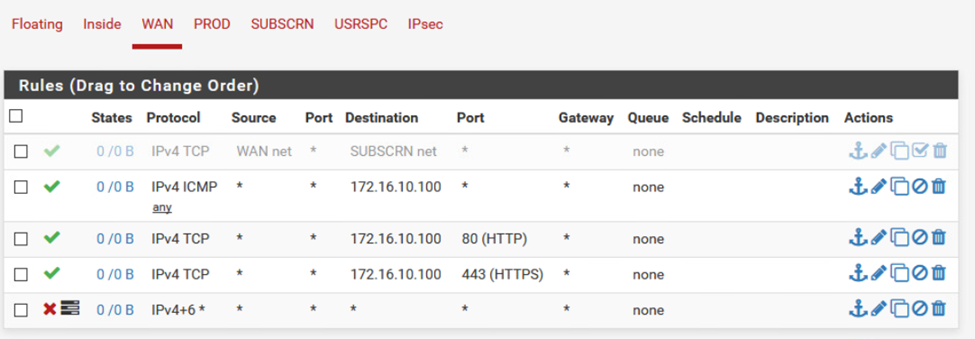
Lastly, the network firewall was configured. The firewall is running PFSENSE, which is performing NAT functions, as well as acting as the default gateway for multiple subnets. Since the only host that should be reachable from outside the organization is Prod-Joomla, rules were added to allow only communication via HTTP and HTTPS. All other traffic will be dropped from the WAN interface.
It was at this point that all my checks turned green and technically I was mission complete.
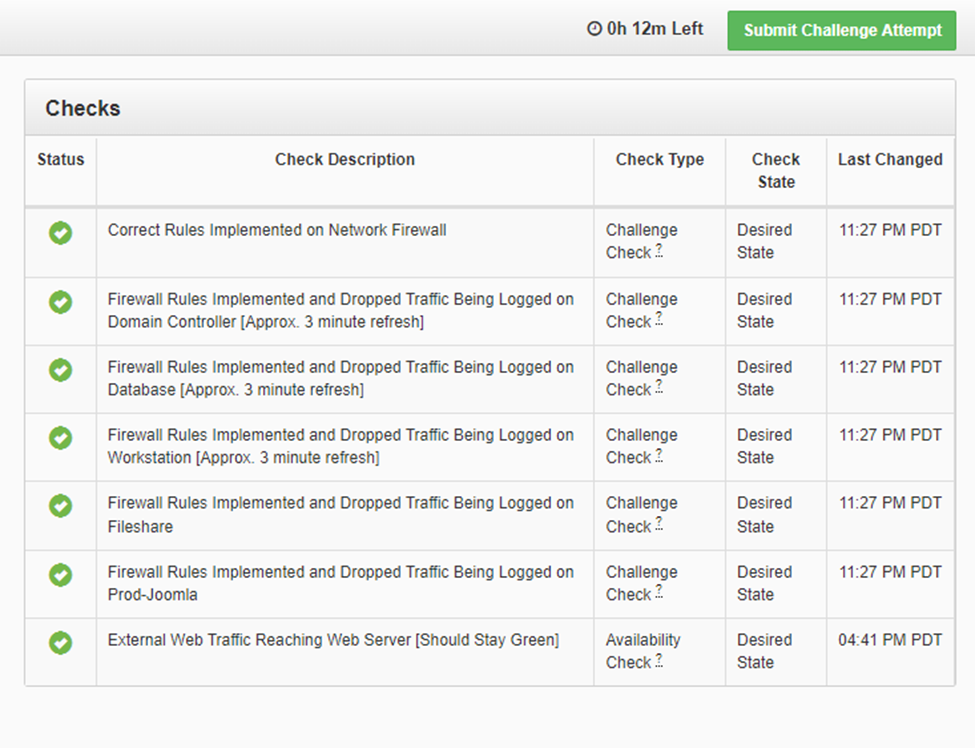
I could stop, but I decided to see what else I could harden before running out of time.
The IPSEC portion of the firewall rules was allowing any-to-any. While unlikely that the secret would be made available to outside entities, explicit rules were added for the MSP and store sites. Old rules were left in place but disabled, and a deny all rule was added.
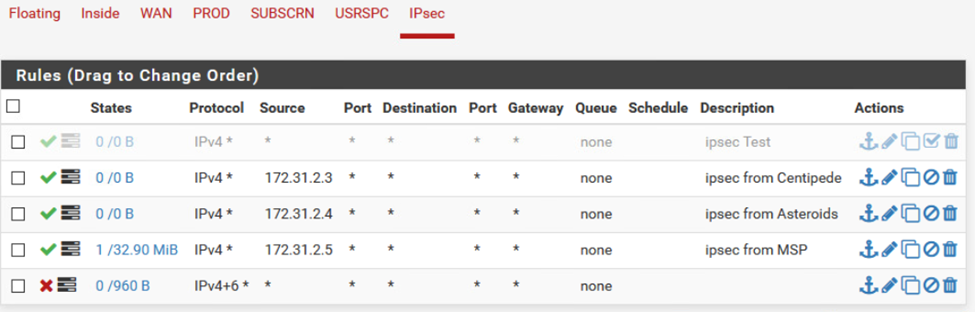
I also added deny all rules to each of the network interfaces PROD, SUBSCRN, and USRSPC, but I had to submit the assignment before I could get more screenshots.
Well, that’s it. Like I said, I had a lot of fun reinforcing old skills and interpreting what certain things meant. I will be making this a regular thing, as long as I have access through WGU. It looks like the next challenge is 10/1 – 10/2, so I will see you then for Challenge 18 – Executable Excavation.
Comments are closed.